persistent cross-site scripting (XSS) vulnerability in a popular site that hosts video content enabled an attacker to carry out a distributed denial-of-service (DDOS) attack against a different site, according to California-based website security company Incapsula, which helped mitigate the Thursday attack.
The video content website is one of the largest and most popular and sits in the Alexa top 50, according to a Thursday post by Ronen Atias, a security researcher with Incapsula, who explained that the name of the popular video site and the name of the DDoS target could not be revealed.
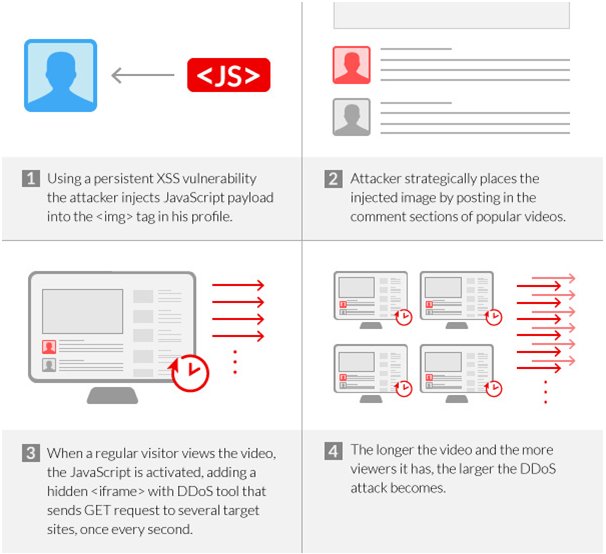
Specific details of the vulnerability also could not be revealed, at least not until it is fixed, but Atias did explain how the attack worked. He said it began with the attacker using the persistent XSS vulnerability to inject a JavaScript payload into the <img> tag for a member’s profile picture on the video website.
“WE USED INCAPSULA’S TECHNOLOGY TO IDENTIFY THE MALICIOUS REQUESTS, INTERCEPT THEM AND RE-ROUTE THEM TO ANOTHER LOCATION WHICH HELD A CUSTOM MADE SCRIPT, [WHICH] TRACED THE REQUEST BACK TO THE DDOS TOOL AND TO THE ABUSED SITE,” ZEIFMAN SAID.
Next, the attacker chose to post in the comments section of the most popular videos. This caused the injected image to be hosted on those pages, so whenever the videos were viewed, the JavaScript activated, GET requests were sent to target sites, and, ultimately, the DDoS was carried out with the unknowing aid of viewers.
In the end, Incapsula’s client was hit by more than 20 million GET requests stemming from more than 22,000 viewers, according to the post. In a Friday email correspondence, Igal Zeifman, product evangelist with Incapsula, explained to SCMagazine.com how the company picked up on the attack.
Post a Comment
Hey Guys If you want anything just email Us.